
Why Cyber Security?
Now more than ever cyber security should be at the forefront when it comes to planning within a business. First there was the nuances to working practices, bought about by COVID -19, and now there is war in Europe bringing about a new threat – cyber based warfare. Battles are also fought virtually, in an attempt to disrupt the infrastructure and organisations that keep countries running. Only last month US President Joe Biden has called on private companies and organisations in the US to “lock their digital doors”, claiming that intelligence suggests Russia is planning a cyber-attack on the US. That aside there have long been threats from other nations it is just that in 2022 these threats have become more pressing due to events of the last few years.
What is cyber security?
The term cyber security refers to the method by which individuals and organisations reduce the risk of being attacked by cyberspace.
The primary function of cyber security is to protect the connected devices we all use (smartphones, laptops, tablets, and computers), and the services we access – both online and at work – from theft or damage.
The goal is also to protect the vast amounts of personal information we store on these devices, and online.
Why is cyber security important?
A local council in the UK has been targeted again in the second cyber-attack directed via an email attachment to a council employee. Causing untold cost to the systems. Public sectors are already stretched financially however if they find themselves in the unfortunate position of having to rebuild servers and systems, it can take months of work. There may be potentially months of lost revenue, in this case with planning applications not being determined.
According to a YouGov survey this month, 71% of Chief Information Officers in the private sector anticipate being more active with Cyber Security, partly due to COVID -19 increasing remote working, but also there is a vast increase in cyber security threats. One of which is the Internet Of Things, or IoT
Now more than ever before it is essential to have a plan for cyber-security across your whole company, which should include training, so all employees are aware of the threats that arise that they may be directly responsible for.
Preparing for cyber-attacks now needs to be high on the agenda.
What are the benefits of cyber security?
The benefits of cyber security is the protection comprehensive digital data security can offer across your business.
It can also protect the individual from personal data breaches – stolen personal information can be misused.
Securing computer systems in an environment where sensitive information is secure helps with not only GDPR, but also can prevent the following:
- Data being exposed from malware or ransomware
- Can prevent date being exposed through hacking or theft
- Protection of intellection property
- Prevention of unauthorised access and loss or deletion of data
- Prevention of damage to hardware
- Prevention of denial of service or DDoS attacks
- Prevention of email attacks
Cybersecurity threats – What you need to know
With nearly every element of society now digitalised, cyber-crime is an inevitable vulnerability that every individual and business faces. Businesses hold large volumes of personal data, and no matter how careful you are there is always a risk of security breaches and that this information can be stolen, misused as in identity theft or misrepresented for the gain of others. There is a risk of reputational damage as well as financial damage to intellectual property
Types of Cybersecurity threat
7 TYPES OF SECURITY THREAT
Malware
The term malware is a general term that includes spyware, ransomware, viruses, and worms. In most cases, malware is activated when a user clicks on a malicious link or attachment, which leads to the installation of malicious software. Once activated, malware can:
- Access to key network components can be blocked (ransomware)
- Place additional harmful software on the network
- Spyware collects and transmits information secretly from the hard drive.
- Destroy individual parts, causing the system to malfunction
Emotet
According to the Cybersecurity and Infrastructure Security Agency (CISA), Emotet is an “advanced, modular banking trojan” used primarily for downloading and dropping other banking Trojans. “Emotet continues to rank among the most costly and destructive malware.”
Denial of Service (DoS / DDoS)
Cyber attacks that flood a computer or network, preventing it from responding to requests are called denial of service (DoS). Distributed DoS (DDoS) attacks from a computer network do the same thing. Flood attacks are often used by cybercriminals to disrupt the “handshake” process and conduct a denial of service attack. Additionally, cyber attackers may use other techniques while a network is disabled. Botnets are types of DDoS where millions of systems can be infected with malware and controlled by hackers. Zombies, sometimes called botnets, target and overpower a target’s processing power. Botnets are difficult to trace due to their geographical locations.
Man In The Middle (MITM)
The man-in-the-middle (MITM) attack occurs when hackers sabotage a two-party transaction. After interrupting the traffic, they can filter and steal data, according to Cisco. MITM attacks often occur when a visitor uses an unsecured public Wi-Fi network. Attackers insert themselves between the visitor and the network, and then use malware to install software and use data maliciously.
Phishing
Phishing attacks use fake communication, such as an email, to trick the receiver into opening it and carrying out the instructions inside, such as providing a credit card number. “The goal is to steal sensitive data like credit card and login information or to install malware on the victim’s machine,” Cisco reports.
Smishing
Or SMS phishing when a malicious link is sent to a mobile device in SMS or text format to try and gather confidential information such as credit card details, passwords or social security numbers.
SQL injection
A Structured Query Language (SQL) injection is a type of cyber attack that results from inserting malicious code into a server that uses SQL. When infected, the server releases information. Submitting the malicious code can be as simple as entering it into a vulnerable website search box.
Password attacks
With the right password, a cyber attacker has access to a wealth of information. Social engineering is a type of password attack that Data Insider defines as “a strategy cyber attackers use that relies heavily on human error and often involves tricking people into breaking standard security practices.” Other types of password attacks or scams include gaining unauthorized access by gaining entry to a password’s database or outright guessing.
How to protect your company from cyber crime
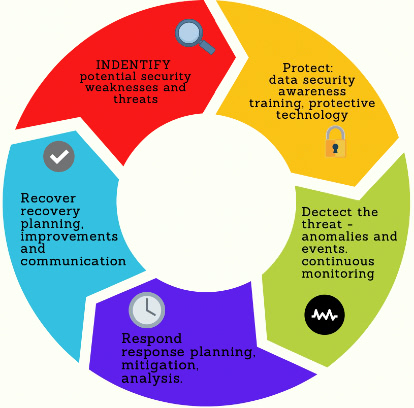
There are some preventative measures that can be implemented and security solutions that can be adopted, to help protect your company’s information security. From deploying training and building awareness of scams to tighter network security, and keeping antivirus software updated.
It is important to consider security standards, procedures and systems and tools that protect your applications through a risk management plan. It is essential to consider the below:
- Authentication
- Authorization
- Antivirus Programs
- Antispyware Software
- Encryption Programs
- Firewalls
- Application Security Testing
Also, it is crucial to consider;
- Raise cybersecurity awareness within your business. Training and an understanding of cybersecurity best practices is essential for all members of a business to understand their part in keeping cyber-secure. Talk about Cybersecurity procedure and the necessity for individuals to – for example – only install trusted applications. Engage around being part of the first defence against cyber attacks. Educate around types of cyber attack; phishing and Smishing. Use spam filters and anti- phishing software to
- Protect access to your critical assets – protect access from remote devices, handle passwords securely, use the principle of least privilege.
- Protect your sensitive data – Build a robust cybersecurity policy and protected network. By having a documented policy all individuals will have access to one document without any ambiguity. This should have all cybersecurity measures listed and should be updated by the allocated cybersecurity professional within the organisation.
- Protect access with efficient identity management. As well as password protecting it is necessary to consider multi-factor authentication and biometric security
- Build a robust cyber security policy and protected network
- It is also worth noting that a good security provider will be able to guide you through the implementation process.
Examples of companies who have suffered from cyber crime
One of the most far reaching and memorable cyber attacks was the ‘Wanna Cry’ ransomware attack in 2017. The initial point of ‘injection’ was thought to be in North Korea, and went on to affect 230,000 computers in 150 countries. The NHS was also a victim, and the malware caused 39 NHS trusts to be simultaneously affected. It was eventually stopped by Marcus Hutchins who found a flaw in the malware code, and managed to put it to a halt. On the anniversary of this attack Marcus was quoted as saying’ many lessons have been learnt from this attack. A great deal of upgrades and security measure have been put in place across many businesses since this time however, many businesses still believe that these ransomware attacks will not affect them.’ In fact the World Economic Forum has this month said that ransomware attacks are up 435% in the last 2 years. This is a very troubling statistic, and one that most business leaders would be well advised not to ignore…
Do you need help to improve cyber security in your organisation?
Contact the Stream Networks Cyber Security Team about our CyberSecurity solutions now.

